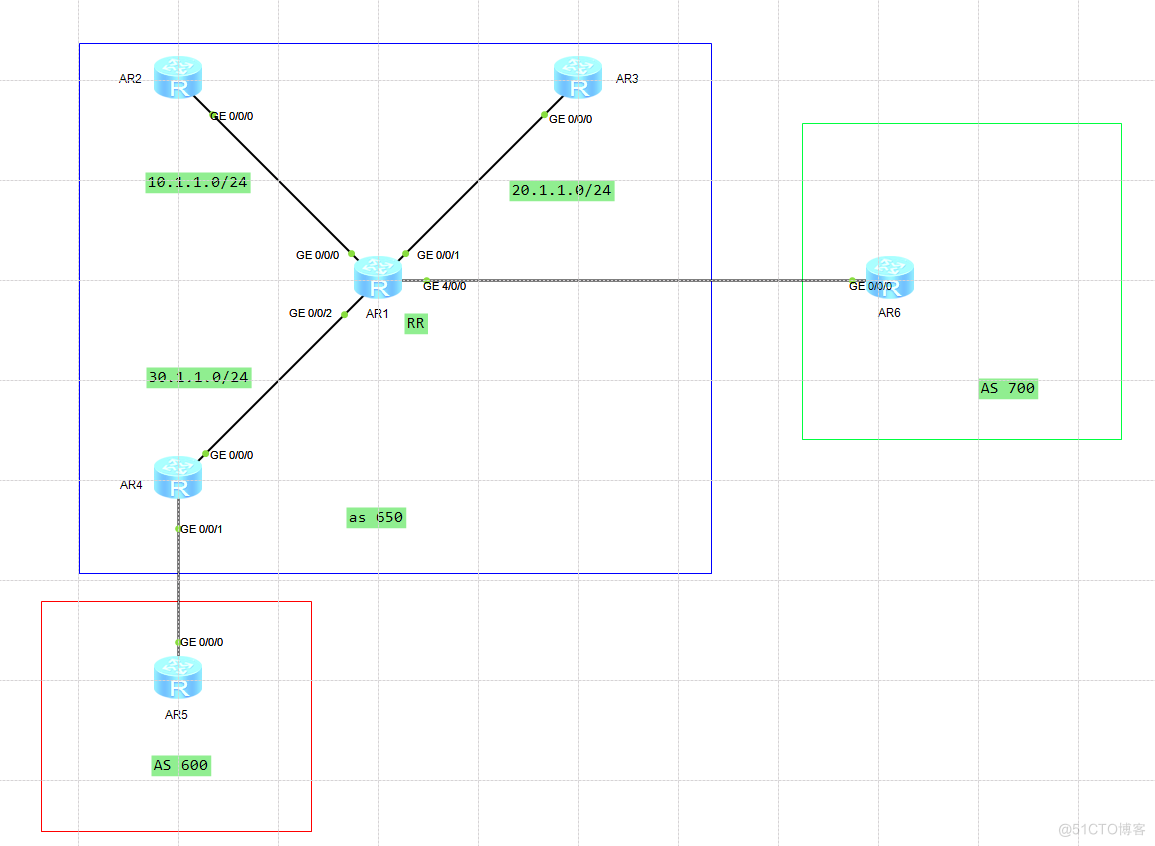
核心技术
1、路由反射规则
1)如果路由反射器从自己的非客户对等体学习到一条IBGP路由,则它会将该路由反射给所有客户机
2)如果路由反射器从EBGP学习到一条路由,则它会将该路由反射给所有客户机
3)如果路由反射器从自己的客户学习到一条IBGP路由,则它会将该路由反射给所有非客户,以及除了该客户以外的其他所有客户
4)如果路由反射器从自己的客户学习到一条EBGP路由,则它会将该路由反射给所有非客户,以及除了该客户以外的其他所有客户
5)如果路由反射器学习自EBGP对等体,则发送给所有客户、非客户IBGP对等体
四字方针:非非不传
配置内容
R1:
display current-configuration
[V200R003C00]
#
sysname r1
#
board add 0/4 4GET
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 20.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 30.1.1.1 255.255.255.0
#
interface服务器托管网 GigabitEthernet4/0/0
ip address 50.1.1.1 255.255.255.0
#
interface GigabitEthernet4/0/1
#
interface GigabitEthernet4/0/2
#
interface GigabitEthernet4/0/3
#
interface NULL0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface LoopBack1
ip address 172.1.1.1 255.255.255.255
#
bgp 650
router-id 1.1.1.1
undo default ipv4-unicast
peer 2.2.2.2 as-number 650
peer 2.2.2.2 connect-interface LoopBack0
peer 3.3.3.3 as-number 650
peer 3.3.3.3 connect-interface LoopBack0
peer 4.4.4.4 as-number 650
peer 4.4.4.4 connect-interface LoopBack0
peer 50.1.1.2 as-number 700
#
ipv4-family unicast
undo synchronization
network 172.1.1.1 255.255.255.255
network 172.168.1.1 255.255.255.255
peer 2.2.2.2 enable
peer 2.2.2.2 reflect-client //路由反射器客户
peer 2.2.2.2 next-hop-local
peer 3.3.3.3 enable
peer 3.3.3.3 reflect-client//路由反射器客户
peer 3.3.3.3 next-hop-local
peer 4.4.4.4 enable
peer 4.4.4.4 reflect-client//路由反射器客户
peer 4.4.4.4 next-hop-local
peer 50.1.1.2 enable
#
ospf 100 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 10.1.1.0 0.0.0.255
network 20.1.1.0 0.0.0.255
network 30.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R2:
display current-configuration
[V200R003C00]
#
sysname r2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 10.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
bgp 650
router-id 2.2.2.2
peer 1.1.1.1 as-number 650
peer 1.1.1.1 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 1.1.1.1 enable
#
ospf 100 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 10.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R3:
display current-configuration
[V200R003C00]
#
sysname r3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 20.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
bgp 650
router-id 3.3.3.3
peer 1.1.1.1 as-number 650
peer 1.1.1.1 connect-interface LoopBack0
#
ipv4-family unicast
undo synchronization
peer 1.1.1.1 enable
#
ospf 100 router-id 3.3.3.3
area 0.0.0.0
network 3.3.3.3 0.0.0.0
network 20.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R4:
display current-configuration
[V200R003C00]
#
sysname r4
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load flash:/portalpage.zip
#
drop illegal-mac alarm
#
wlan ac-global carrier id other ac id 0
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 30.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 40.1.1.1 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
interface LoopBack1
ip address 192.168.1.1 255.255.255.255
#
bgp 650
router-id 4.4.4.4
peer 1.1.1.1 as-number 650
peer 1.1.1.1 connect-interface LoopBack0
peer 40.1.1.2 as-number 600
#
ipv4-family unicast
undo synchronization
network 服务器托管网192.168.1.1 255.255.255.255
peer 1.1.1.1 enable
peer 1.1.1.1 next-hop-local
peer 40.1.1.2 enable
#
ospf 100 router-id 4.4.4.4
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 30.1.1.0 0.0.0.255
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R5:
display current-configuration
[V200R003C00]
#
sysname r5
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 40.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
interface LoopBack1
ip address 172.16.2.1 255.255.255.255
#
bgp 600
router-id 5.5.5.5
peer 40.1.1.1 as-number 650
#
ipv4-family unicast
undo synchronization
network 172.16.2.1 255.255.255.255
peer 40.1.1.1 enable
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
R6:
display current-configuration
[V200R003C00]
#
sysname r6
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 50.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
interface LoopBack0
ip address 6.6.6.6 255.255.255.255
#
interface LoopBack1
ip address 172.16.3.1 255.255.255.255
#
bgp 700
router-id 6.6.6.6
peer 50.1.1.1 as-number 650
#
ipv4-family unicast
undo synchronization
network 172.16.3.1 255.255.255.255
peer 50.1.1.1 enable
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
服务器托管,北京服务器托管,服务器租用 http://www.fwqtg.net
机房租用,北京机房租用,IDC机房托管, http://www.fwqtg.net
相关推荐: Python主题建模LDA模型、t-SNE 降维聚类、词云可视化文本挖掘新闻组数据集|附代码数据
全文链接:http://tecdat.cn/?p=24376 最近我们被客户要求撰写关于主题建模的研究报告,包括一些图形和统计输出。 在这篇文章中,我们讨论了基于gensim 包来可视化主题模型 (LDA) 的输出和结果的技术 介绍 我们遵循结构化的工作流程…

